The Iranian state-sponsored menace actor often known as MuddyWater has been attributed to a brand new swarm of assaults concentrating on Turkey and the Arabian Peninsula with the objective of deploying distant entry trojans (RATs) on compromised techniques.
“The MuddyWater supergroup is extremely motivated and might use unauthorized entry to conduct espionage, mental property theft, and deploy ransomware and harmful malware in an enterprise,” Cisco Talos researchers Asheer Malhotra, Vitor Ventura, and Arnaud Zobec mentioned in a report revealed at the moment.
The group, which has been energetic since not less than 2017, is understood for its assaults on varied sectors that assist additional advance Iran’s geopolitical and nationwide safety aims. In January 2022, the U.S. Cyber Command attributed the actor to the nation’s Ministry of Intelligence and Safety (MOIS).
MuddyWater can be believed to be a “conglomerate of a number of groups working independently somewhat than a single menace actor group,” the cybersecurity agency added, making it an umbrella actor within the vein of Winnti, a China-based superior persistent menace (APT).
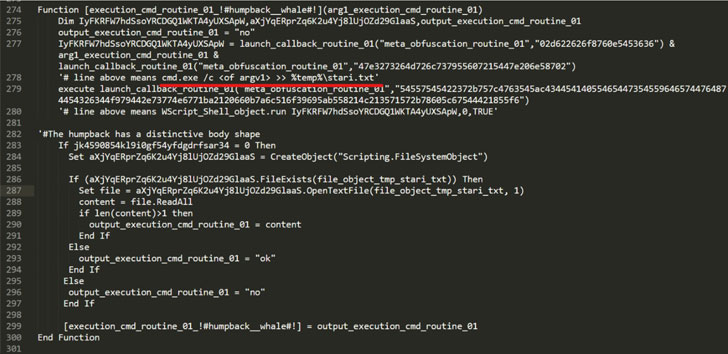
The most recent campaigns undertaken by the hacking crew contain using malware-laced paperwork delivered by way of phishing messages to deploy a distant entry trojan known as SloughRAT (aka Cover by CISA) able to executing arbitrary code and instructions acquired from its command-and-control (C2) servers.
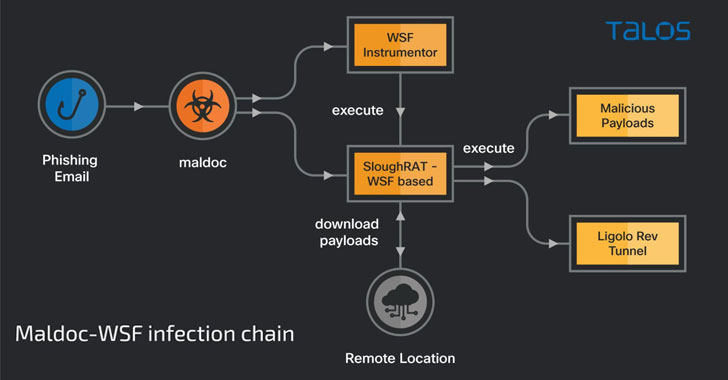
The maldoc, an Excel file containing a malicious macro, triggers the an infection chain to drop two Home windows Script Information (.WSF) on the endpoint, the primary considered one of them performing because the instrumentor to invoke and execute the next-stage payload.
Additionally found are two further script-based implants, one written in Visible Fundamental and the opposite coded in JavaScript, each of that are engineered to obtain and run malicious instructions on the compromised host.
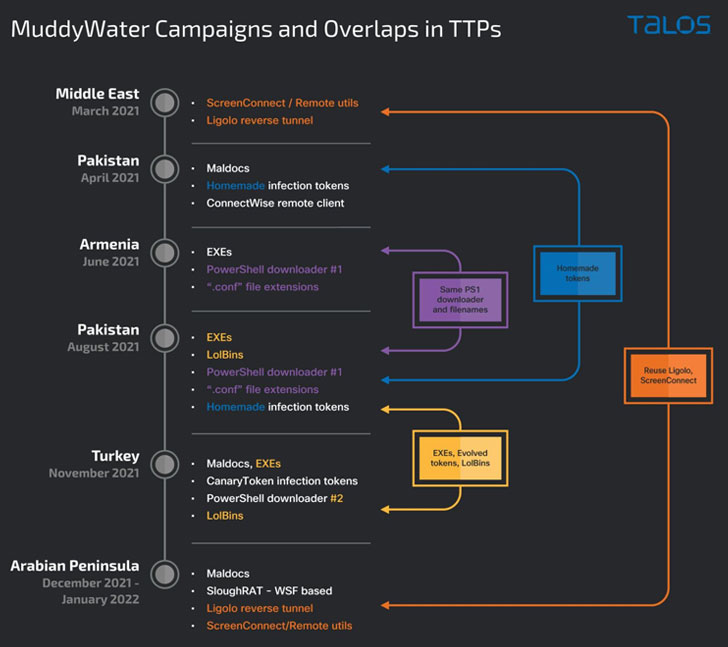
Moreover, the most recent set of intrusions marks a continuation of a November 2021 marketing campaign that struck Turkish personal organizations and governmental establishments with PowerShell-based backdoors to assemble data from its victims, even because it reveals overlaps with one other marketing campaign that befell in March 2021.
The commonalities in techniques and strategies adopted by the operators have raised the chance that these assaults are “distinct, but associated, clusters of exercise,” with the campaigns leveraging a “broader TTP-sharing paradigm, typical of coordinated operational groups,” the researchers famous.
A second phishing assault sequence between December 2021 and January 2022 involved the deployment of VBS-based malicious downloaders utilizing scheduled duties created by the adversary, enabling the execution of payloads retrieved from a distant server. The outcomes of the command are subsequently exfiltrated again to the C2 server.
“Whereas they share sure strategies, these campaigns additionally denote individuality in the best way they have been performed, indicating the existence of a number of sub-teams beneath the Muddywater umbrella — all sharing a pool of techniques and instruments to choose and select from,” the researchers concluded.