Authored by Oliver Devane, Vallabh Chole, and Aayush Tyagi
McAfee has not too long ago noticed a number of malicious Chrome Extensions which, as soon as put in, will redirect customers to phishing websites, insert Affiliate IDs and modify respectable web sites to exfiltrate personally identifiable data (PII) information. In keeping with the Google Extension Chrome Retailer, the mixed set up base is 80,000
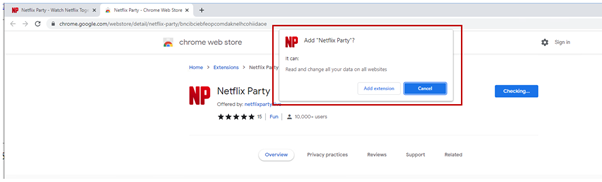
One extension, ‘Netflix Get together’, mimics the unique Netflix Get together extension, which permits teams of individuals to observe Netflix reveals on the identical time. Nevertheless, this model displays all of the web sites you go to and performs a number of malicious actions.
The malicious actor behind the extensions has created a number of Twitter accounts and pretend evaluate web sites to deceive customers into trusting and set uping the extensions.
The sufferer might be tricked into putting in the extension and their information might be stolen when shopping a present card web site.
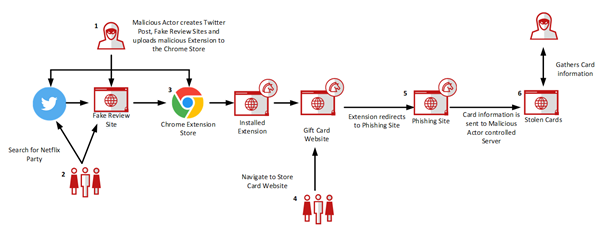
The small print of every step are as follows:
- The perpetrator creates malicious extensions and provides them to the Chrome Extension Retailer. They create faux web sites to evaluate the extensions and pretend Twitter accounts to publicize them.
- A sufferer could carry out an internet or Twitter seek for Netflix Get together, learn the evaluate and click on on a hyperlink that can make them the Google Chrome Retailer.
- They click on to put in the Extension and settle for the permissions.
- The sufferer will both carry out an internet search or straight navigate to the present card web site. The Extension will establish the web site and redirect them to the phishing web page.
- The sufferer will enter their present card data on the phishing web page.
- The present card data is posted to the server to which the malicious actor has entry. They’ll now use or promote the stolen information and the sufferer will lose their funds.
Technical Evaluation
This part incorporates the technical evaluation of the malicious chrome extension “bncibciebfeopcomdaknelhcohiidaoe“.
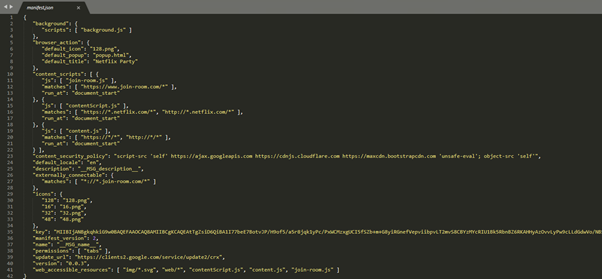
Manifest.json
The manifest.json file incorporates the permissions of the extension. The ‘unsafe-eval’ permission within the ‘content_security_policy’ and the allowed use of content material.js on any web site visited by the person is of explicit concern
Background.js
When the extension is put in, the background.js script might be loaded. This file makes use of a easy obfuscation strategy of placing all of the code on one line which makes it troublesome to learn. That is simply cleaned up by utilizing a code beautifier and the picture beneath reveals the obfuscated script on the primary line and the cleaned-up code beneath the pink arrow.
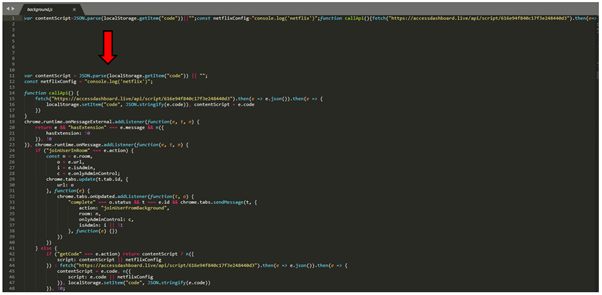
This script accesses https://accessdashboard[.]stay to obtain a script and retailer it as variable ‘code’ in Chrome’s native storage. This saved variable is then referenced within the content material.js script, which is executed on each visited web site.
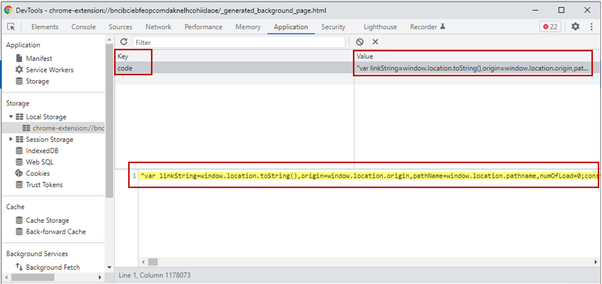
Content material.js
After beautification, we see the code will learn the malicious script from the ‘code’ variable which was beforehand saved.
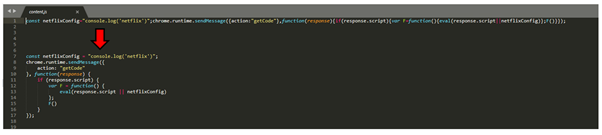
‘Code’
The malicious code has three important capabilities, redirection for phishing, modifying of cookies so as to add AffiliateIDs, and modifying of web site code so as to add chat home windows.
![]()
Redirection for Phishing
Redirection for phishing works by checking if the URL being accessed matches an inventory, and conditionally redirects to a malicious IP that hosts the phishing web site.
URLs monitored are:
- https[:]//www.goal.com/visitor/gift-card-balance
- https[:]//www.macys.com/account/giftcardbalance
- https[:]//www.nike.com/orders/gift-card-lookup
- https[:]//www.nordstrom.com/nordstrom-gift-cards
- https[:]//www.sephora.com/magnificence/giftcards
- https[:]//www.sephoragiftcardbalance.com
- https[:]//stability.amexgiftcard.com
- https[:]//prepaidbalance.americanexpress.com/GPTHBIWeb/validateIPAction.do?clientkey=retailpercent20salespercent20channel
- https[:]//amexprepaidcard.com
- [:]//secure4.retailer.apple.com/store/giftcard/stability
Upon navigating to one of many above websites, the person might be redirected to 164[.]90[.]144[.]88. An observant person would discover that the URL would have modified to an IP tackle, however some customers could not.
The picture beneath reveals the Apple Phishing web site and the assorted phishing kits being hosted on this server.
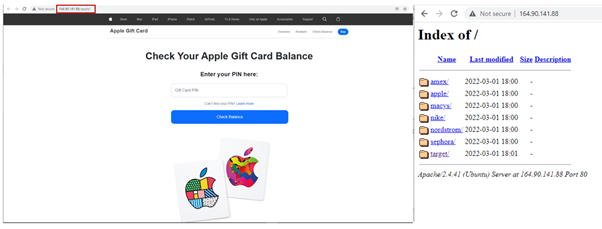
The phishing websites share comparable codes. If a person enters their present card data, the info might be posted to 52.8.106.52. A community seize of the submit request is proven beneath:
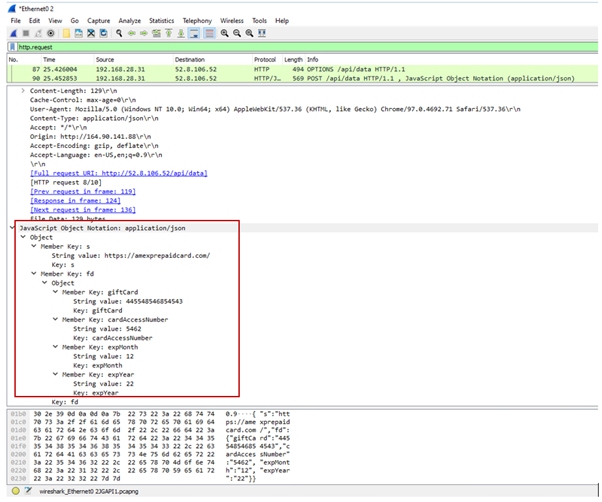
Modifying of cookies so as to add AffiliateIDs
The second malicious perform incorporates AIPStore which is a dictionary containing an inventory of URLs and their respective monetizing websites which give affiliate IDs. This perform works by loading new tabs which can end in cookies being set on the visited websites. The movement beneath describes how the extension will work.
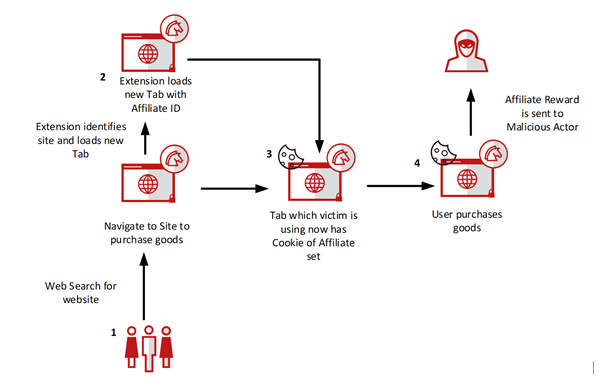
- A person navigates to a retail web site
- If the retail web site is contained within the AIPStore keymap, the extension will load a brand new tab with a hyperlink to a monetizing web site which units the cookie with the affiliate ID. The brand new tab is then closed, and the cookie will persist.
- The person might be unaware {that a} cookie would have been set and they’re going to proceed to browse the web site.
- Upon buying any items, the Affiliate ID might be acknowledged by the positioning vendor and fee might be despatched to the Affiliate ID proprietor which might be the Malicious Actor
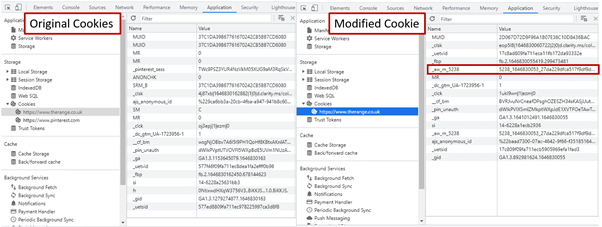
The left picture beneath reveals the unique web site with no affiliate cookie, the one on the fitting highlights the cookie that has been added by the extension.
Chat Home windows
The ultimate perform checks an inventory of URLs being accessed and in the event that they match, a JS script might be injected into the HTML code which can end in a chat window being displayed. The picture beneath reveals the injected script and the chat window.
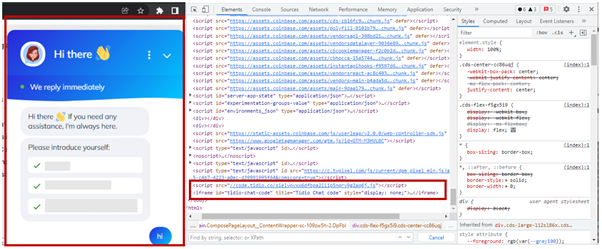
The chat window could also be utilized by the malicious actor to request PII information, bank card, and product key data.
Conclusion
This risk is an effective instance of the lengths malicious actors will go to trick customers into putting in malware equivalent to creating Twitter accounts and pretend evaluate web sites.
McAfee advises its clients to be cautious when putting in Chrome Extensions and take note of the permissions that they’re requesting.
The permissions might be proven by Chrome earlier than the set up of the Extension. Clients ought to take additional steps to confirm the authenticity if the extension is requesting permissions that allow it to run on each web site you go to such because the one detailed on this weblog
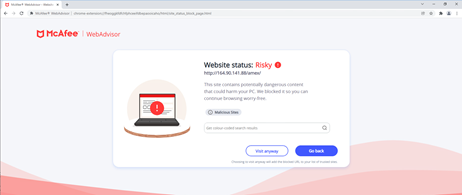
McAfee clients are protected towards the malicious websites detailed on this weblog as they’re blocked with McAfee WebAdvisor as proven beneath.
The Malicious code throughout the extension is detected as Phish-Extension. Please carry out a ‘Full’ scan by way of the product.
| Sort | Worth | Product | Detected |
| URL – Phishing Websites | 164.90.141.88/* | McAfee WebAdvisor | Blocked |
| Chrome Extension | netflix-party – bncibciebfeopcomdaknelhcohiidaoe | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | teleparty – flddpiffdlibegmclipfcnmaibecaobi | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | hbo-max-watch-party – dkdjiiihnadmgmmfobidmmegidmmjobi | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | prime-watch-party – hhllgokdpekfchhhiknedpppjhgicfgg | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | private-watch-party – maolinhbkonpckjldhnocgilkabpfodc | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | hotstar-ad-blocker – hacogolfhplehfdeknkjnlblnghglfbp | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | hbo-ad-blocker – cbchmocclikhalhkckeiofpboloaakim | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | blocksite – pfhjfcifolioiddfgicgkapbkfndaodc | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | hbo-enhanced – pkdpclgpnnfhpapcnffgjbplfbmoejbj | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | hulu-watch-party – hkanhigmilpgifamljmnfppnllckkpda | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | disney-plus-watch-party – flapondhpgmggemifmemcmicjodpmkjb | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | spotify-ad-blocker – jgofflaejgklikbnoefbfmhfohlnockd | Whole Safety and LiveSafe | Phish-Extension |
| Chrome Extension | ott-party – lldibibpehfomjljogedjhaldedlmfck | Whole Safety and LiveSafe | Phish-Extension |

